Consideration! On the off chance that you utilize Amazon's voice aide Alexa in you savvy speakers, simply opening a blameless looking web-connection could let aggressors introduce hacking aptitudes on it and spy on your exercises distantly.
Check Point cybersecurity analysts—Dikla Barda, Roman Zaikin and Yaara Shriki—today revealed extreme security weaknesses in Amazon's Alexa remote helper that could deliver it defenseless against various pernicious assaults.
the "adventures could have permitted an aggressor to expel/introduce abilities on the focused on casualty's Alexa account, get to their voice history and procure individual data through expertise connection when the client conjures the introduced aptitude."
"Shrewd speakers and menial helpers are typical for such an extent that it's not entirely obvious exactly how much close to home information they hold, and their job in controlling other keen gadgets in our homes," Oded Vanunu, head of item weaknesses research, said.
"In any case, programmers consider them to be passage focuses into people groups' carries on with, allowing them the chance to get to information, listen in on discussions or lead different malignant activities without the proprietor staying alert," he included.
Amazon fixed the weaknesses after the specialists uncovered their discoveries to the organization in June 2020.
A XSS Flaw in One of Amazon's Subdomains :
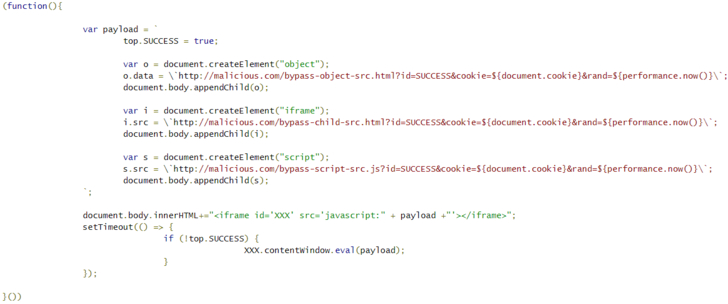
Check Point said the blemishes originated from a misconfigured CORS strategy in Amazon's Alexa portable application, in this manner possibly permitting enemies with code-infusion capacities on one Amazon subdomain to play out a cross-area assault on another Amazon subdomain.
Put in an unexpected way, fruitful misuse would have required only a single tick on an Amazon interface that has been uncommonly created by the assailant to guide clients to an Amazon subdomain that is powerless against XSS assaults.
What's more, the specialists found that a solicitation to recover a rundown of all the introduced abilities on the Alexa gadget additionally restores a CSRF token in the reaction.
The basic role of a CSRF token is to forestall Cross-Site Request Forgery assaults in which a pernicious connection or program causes a confirmed client's internet browser to play out an undesirable activity on a genuine site.
This happens on the grounds that the site can't separate between real demands and manufactured solicitations.
In any case, with the token under lock and key, a troublemaker can make substantial solicitations to the backend worker and perform activities for the casualty's benefit, for example, introducing and empowering another aptitude for the casualty distantly.
To put it plainly, the assault works by provoking the client to tap on a noxious connection that explores to an Amazon subdomain ("track.amazon.com") with a XSS defect that can be abused to accomplish code-infusion.
The assailant at that point utilizes it to trigger a solicitation to "skillsstore.amazon.com" subdomain with the casualty's accreditations to get a rundown of all introduced aptitudes on the Alexa account and the CSRF token.
In the last stage, the endeavor catches the CSRF token from the reaction and utilizations it to introduce an ability with a particular aptitude ID on the objective's Alexa account, covertly evacuate an introduced expertise, get the casualty's voice order history, and even access the individual data put away in the client's profile.
The Need for IoT Security :
With the worldwide brilliant speaker showcase size anticipated to reach $15.6 billion by 2025, the examination is another motivation behind why security is critical in the IoT space.
As remote helpers become more unavoidable, they are progressively ending up being rewarding focuses for aggressors hoping to take touchy data and upset shrewd home frameworks.
"IoT gadgets are innately helpless and still need sufficient security, which makes them appealing focuses to danger entertainers," the specialists finished up.
"Cybercriminals are consistently searching for better approaches to break gadgets, or use them to contaminate other basic frameworks. Both the scaffold and the gadgets fill in as section focuses. They should be kept made sure about consistently to shield programmers from invading our shrewd homes."