In the event that you haven't as of late refreshed your Chrome, Opera, or Edge internet browser to the most recent accessible rendition, it would be a brilliant plan to do as such as fast as could reasonably be expected.
Cybersecurity analysts on Monday revealed insights regarding a zero-day blemish in Chromium-based internet browsers for Windows, Mac and Android that could have permitted aggressors to completely sidestep Content Security Policy (CSP) rules since Chrome 73.
Followed as CVE-2020-6519 (appraised 6.5 on the CVSS scale), the issue originates from a CSP sidestep that outcomes in subjective execution of vindictive code on track sites.
As per PerimeterX, the absolute most mainstream sites, including Facebook, Wells Fargo, Zoom, Gmail, WhatsApp, Investopedia, ESPN, Roblox, Indeed, TikTok, Instagram, Blogger, and Quora, were defenseless to the CSP sidestep.
Curiously, apparently a similar imperfection was likewise featured by Tencent Security Xuanwu Lab over a year prior, only a month after the arrival of Chrome 73 in March 2019, however was never tended to until PerimeterX revealed the issue before this March.
After the discoveries were unveiled to Google, the Chrome group gave a fix for the weakness in Chrome 84 update (rendition 84.0.4147.89) that started turning out on July 14 a month ago.
CSP is an additional layer of security that identifies and moderate particular kinds of assaults, including Cross-Site Scripting (XSS) and information infusion assaults. With CSP rules, a site can command the casualty's program to play out certain customer side checks with a mean to square explicit contents that are intended to abuse the program's trust of the substance got from the worker.
Given that CSP is the essential technique utilized by site proprietors to authorize
information security strategies and forestall the execution of pernicious contents, a CSP sidestep can successfully put client information in danger.
This is accomplished by indicating the areas that the program ought to consider to be substantial wellsprings of executable contents, with the goal that a CSP-perfect program just executes contents stacked in source records got from those permit recorded spaces, disregarding all others.
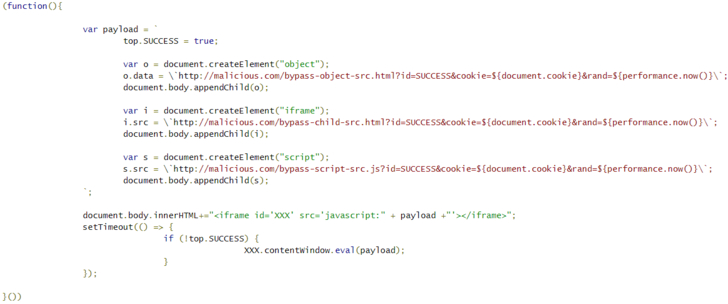
The blemish found by Tencent and PerimeterX goes around the designed CSP for a site by just passing a malevolent JavaScript code in the "src" property of a HTML iframe component.
It's significant that sites like Twitter, Github, LinkedIn, Google Play Store, Yahoo's Login Page, PayPal, and Yandex were not discovered helpless since the CSP approaches were actualized utilizing a nonce or hash to permit the execution of inline contents.
"Having a weakness in Chrome's CSP implementation system doesn't legitimately imply that locales are penetrated, as the assailants additionally need to figure out how to get the pernicious content called from the site (which is the reason the weakness was delegated medium seriousness)," PerimeterX's Gal Weizman noted.
While the ramifications of the weakness stay obscure, clients must refresh their programs to the most recent adaptation to ensure against such code execution. Site proprietors, as far as it matters for them, are prescribed to utilize nonce and hash capacities of CSP for included security.
Other than this, the most recent Chrome update 84.0.4147.125 for Windows, Mac, and Linux frameworks additionally fixes 15 other security weaknesses, 12 of which are evaluated 'high' and two 'low' in seriousness.
This is accomplished by indicating the areas that the program ought to consider to be substantial wellsprings of executable contents, with the goal that a CSP-perfect program just executes contents stacked in source records got from those permit recorded spaces, disregarding all others.
The blemish found by Tencent and PerimeterX goes around the designed CSP for a site by just passing a malevolent JavaScript code in the "src" property of a HTML iframe component.
It's significant that sites like Twitter, Github, LinkedIn, Google Play Store, Yahoo's Login Page, PayPal, and Yandex were not discovered helpless since the CSP approaches were actualized utilizing a nonce or hash to permit the execution of inline contents.
"Having a weakness in Chrome's CSP implementation system doesn't legitimately imply that locales are penetrated, as the assailants additionally need to figure out how to get the pernicious content called from the site (which is the reason the weakness was delegated medium seriousness)," PerimeterX's Gal Weizman noted.
While the ramifications of the weakness stay obscure, clients must refresh their programs to the most recent adaptation to ensure against such code execution. Site proprietors, as far as it matters for them, are prescribed to utilize nonce and hash capacities of CSP for included security.
Other than this, the most recent Chrome update 84.0.4147.125 for Windows, Mac, and Linux frameworks additionally fixes 15 other security weaknesses, 12 of which are evaluated 'high' and two 'low' in seriousness.