Previous Vice President and hypothetical Democratic presidential chosen one Joe Biden said he would make cruel move against any country express that endeavored to interfere in the U.S. presidential political decision, "regardless of whether by hacking casting a ballot frameworks and databases, laundering cash into our political framework, efficiently spreading disinformation, or attempting to plant question about the trustworthiness of our races." On the off chance that Biden picks up the White House in November, he will treat remote impedance in the political race "as an antagonistic demonstration that altogether influences the connection between the United States and the meddling country's legislature," the VP wrote in an announcement discharged Monday evening.
"I will coordinate the U.S. Knowledge Community to report freely and in a convenient way on any endeavors by outside governments that have meddled, or endeavored to meddle, with U.S. races." Biden promised to "influence every suitable instrument of national force" and completely utilize official position to force generous and enduring costs discipline on state entertainers, including "money related division sanctions, resource freezes, digital reactions, and the introduction of defilement." The previous VP as of late employed Chris DeRusha, previous boss security official with the State of Michigan, as his crusade's CISO. DeRusha has less than four months to execute his cybersecurity vision before Election Day shows up, confused by a pandemic that has modified how battles work. The previous VP's announcement came as House and Senate Democratic pioneers discharged the substance of a letter sent a week ago to FBI Director Christopher Wray mentioning a counterintelligence instructions for Congress on endeavors by outside elements to meddle in the 2020 political race. "We are gravely worried, specifically, that Congress gives off an impression of being the objective of a deliberate outside obstruction battle, which looks to wash and intensify disinformation so as to impact congressional action, open discussion and the presidential political decision," Sen. Throw Schumer, D-N.Y.;
House Speaker Nancy Pelosi, D-Calif.; Senate Intelligence Committee Co-director Mark Warner, D-Va.; and House Intelligence Committee Chairman Adam Schiff, D-Calif., wrote to Wray. Among their interests is that remote entertainers are piping disinformation into an examination concerning the previous VP's child Hunter Biden's job on the leading group of Ukrainian organization Burisma Holdings being driven by Sen. Ron Johnson, R-Wis., and administrator of the Senate Homeland Security and Governmental Affairs Committee, a Politico report said. "Board of trustees staff has just mentioned and gotten a staff preparation on this issue, and Chairman Johnson has mentioned an extra instructions at the part level," the report refered to a Johnson representative as saying.
Security analysts at IBM X-Force Incident Response Intelligence Services (IRIS) have gotten generally 40GB of recordings and different documents having a place with a top Iranian hacking gathering. The information trove found by IBM X-Force IRIS analysts contained approximately five hours of video preparing that seems to have been recorded straightforwardly from the screens of programmers working for a state-supported gathering that it calls ITG18 (likewise called Charming Kitten, Phosphorus, or APT35), which has been related with focusing of pharmaceutical organizations and the U.S. presidential crusades. The IBM X-Force IRIS analysts found the recordings on a virtual private cloud server that were coincidentally transferred by programmers in May because of a miss configuration of security settings. During a three-day time frame in May 2020, IBM X-Force IRIS found the 40GBs of video and information documents being transferred to a server that facilitated various ITG18 spaces utilized in the prior 2020 action. "Infrequently are there chances to see how the administrator carries on behind the console, and much rarer despite everything are there chronicles the administrator self-delivered demonstrating their activities. Yet, that is actually what X-Force IRIS revealed on an ITG18 administrator whose OPSEC disappointments give a novel in the background investigate their strategies, and possibly, their legwork for a more extensive activity that is likely in progress," Allison Wikoff, Strategic Cyber Threat Analyst, IBM Security said. A portion of the casualties in the recordings included traded off records of an individual from the U.S.
Naval force and a staff official with almost two many years of administration in the Hellenic Navy, the maritime power of Greece. What's more, it additionally included fruitless phishing endeavors coordinated against individual records of an anonymous Iranian-American giver and U.S. State Department authorities. "A portion of the recordings demonstrated the administrator overseeing enemy made records while others indicated the administrator testing access and exfiltrating information from recently undermined accounts," the analysts said. The video documents revealed by IBM X-Force IRIS were work area accounts utilizing a device called Bandicam, extending from 2 minutes to 2 hours. The timestamps of the documents demonstrated the recordings were recorded around one day preceding being transferred to the ITG18-worked server. In five of the video records, named "AOL.avi", "Aol Contact.avi", "Gmail.avi", "Yahoo.avi", "Hotmail.avi", the administrator utilizes a Notepad document containing one qualification for every stage, and video-by-video reordered them into the related site. The administrator proceeded onward to show how to exfiltrate different datasets related with these stages including contacts, photographs, and related distributed storage. The administrator additionally altered settings inside the record security segment of each record and added them to Zimbra, a genuine email coordinated effort stage that can join various email accounts into one interface. With Zimbra, the administrator had the option to screen and oversee different traded off email accounts at the same time. A portion of the administrator claimed accounts saw in the preparation recordings gave extra understanding into personas related to ITG18, for example, telephone numbers with Iranian nation codes. IBM X-Force IRIS watched the "Yahoo.avi" video showed profile subtleties for a phony persona, which we will reference as "Persona An" incorporating a telephone number with a +98 nation code, the worldwide nation code for Iran. "Notwithstanding the inspiration, botches by the ITG18 administrator permitted IBM X-Force IRIS to increase significant experiences into how this gathering may achieve activity on its goals and in any case train its administrators. IBM X-Force IRIS considers ITG18 a decided danger bunch with a critical interest in its tasks," the specialists noted. "The gathering has demonstrated determination in its tasks and reliable production of new foundation regardless of numerous open revelations and wide writing about its action." ITG18, which has been dynamic since in any event 2013, fundamentally targets people and substances of key enthusiasm to the Iranian government by utilizing certification reaping and email bargain activities through phishing assaults.
Indeed, Cerberus malware has risen as a danger to clients in the wake of showing up on the Google Play Store. The malware acted like a digital money converter application to deceive clients, in this way arriving at a great many downloads.
Cerberus Posing As Cryptocurrency App
Researchers from Avast discovered Cerberus malware showing up on Google Play Store.
The malware took cover behind a digital money converter application. As clarified in their post, the application apparently focuses on Spanish clients.
It bears the name "Calculadora de Moneda" which interprets as "Money Calculator" in English.
Considering the specialty picked, it appears that malware essentially endeavored to take clients' financial information, which the clients would need to enter while changing over their digital currency to fiat cash.
Quickly, the scientists saw that the application stayed innocuous for a couple of beginning weeks, apparently to assemble clients (or casualties). This likewise permitted the application to get away from security check by Google Play Protect.
Be that as it may, the application bore pernicious malware dropper code which stayed idle at first yet later got dynamic.
The analysts could watch the application speaking with the C&C server to download an extra vindictive APK – the financier.
As to it would work, the analysts expressed
In this last stage, the financier application can sit over a current banking application and trust that the client will sign into their ledger. So, all in all the pernicious Trojan initiates, making a delay over your login screen, and takes all your entrance information.
Besides, the malware would likewise peruse messages apparently to get to two-factor confirmation subtleties. Henceforth, malware could without much of a stretch avoid all security methods.
Malware Disappeared. Be that as it may, Threat Persists…
Though, the dynamic Cerberus malware usefulness showed up for a brief timeframe. Not long after its revelation, the pernicious C&C vanished and the application became innocuous by and by.
In any case, the specialists have clarified that danger on-screen characters may utilize such subtle strategies to remain under the radar for some time.
Despite the fact that this was only a brief period, it's a strategy fraudsters much of the time use to escape assurance and discovery for example constraining the time window where the malevolent action can be found.
Thusly, the clients must stay cautious while downloading any application, particularly the ones managing delicate data, for example, bank subtleties.
With respect to this application, it is astute to quit utilizing this application immediately. No one knows when the culprits would trigger another period of dynamic financial Trojan.
Labyrinth ransomware administrators are caught up with refreshing their rundown of casualties, by focusing on an enormous number of associations consistently. As of late, they professed to have added the Xerox Corporation to their casualty list. Xerox inked with information release episode Xerox, the US-based printing arrangements supplier, purportedly turned into a survivor of a system interruption and information penetrate occurrence. In June, Maze ransomware administrators had focused on the Xerox Corporation and had taken in excess of 100 GB of records before encoding them. As a proof of hack, Maze bunch distributed a lot of 10 screen captures, demonstrating their system shares on the area eu.xerox[.]net, a payoff note, and the registry postings from June 24, which proposed that the assailants approached those systems till June 25, 2020. Labyrinth ransomware administrators had just remembered the name of Xerox for the rundown of the casualties distributed on their break site on June 24. A bustling danger monger Labyrinth ransomware administrators have kept occupied with focused assaults, and advancing their information release site also. Inside the most recent seven day stretch of June, Maze administrators included names of a few associations as their casualties, including VT San Antonio Aerospace, a couple of Club Fitness establishments in Missouri, WorldNet Telecommunications, Caldwell Toyota, Ostermeier FZE, OWL Underwriting, Virtual Guard, Manson Construction Co., Innotech-Execaire, and CPFL systems. Toward the finish of June, Maze administrators had released the information of a few casualty associations including LG Electronics, that would not pay the payment. Alongside that information, Maze pack likewise did a few advancements by posting names of other focused on casualties (Xerox being one of them), without posting and different insights concerning the assault. Fascinating pattern or a fortuitous event Labyrinth administrators have been focusing on associations over a wide spread of areas and topographical districts, which is by all accounts a specially appointed assault procedure. Be that as it may, it has likewise embraced the major event chasing way to deal with target remove enormous payoffs from prominent associations. The gathering typically targets one prominent or high-esteemed casualty consistently, as LG Electronics, Conduent, Pitney Bowes, Cognizant, and others. A few little or medium-sized firms are focused on a practically consistent schedule, according to the increments made to its casualty's rundown.
In what's one of the most inventive hacking efforts, cybercrime groups are presently concealing vindictive code inserts in the metadata of picture records to clandestinely take installment card data entered by guests on the hacked sites. "We discovered skimming code covered up inside the metadata of a picture record (a type of steganography) and secretly stacked by undermined online stores," Malwarebytes analysts said a week ago. "This plan would not be finished without one more fascinating variety to exfiltrate taken Visa information. Indeed, lawbreakers utilized the camouflage of a picture document to gather their plunder." The developing strategy of the activity, generally known as web skimming or a Magecart assault, comes as terrible on-screen characters are finding various approaches to infuse JavaScript contents, including misconfigured AWS S3 information stockpiling containers and abusing content security strategy to transmit information to a Google Analytics account under their influence. Utilizing Steganography to Hide Skimmer Code in EXIF: Relying upon the developing pattern of web based shopping, these assaults ordinarily work by embeddings noxious code into an undermined website, which clandestinely collects and sends client entered information to a cybercriminal's server, hence giving them access to customers' installment data.
In this week-old crusade, the cybersecurity firm found that the skimmer was not just found on an online store running the WooCommerce WordPress module yet was contained in the EXIF (short for Exchangeable Image File Format) metadata for a dubious area's (cddn.site) favicon picture. Each picture comes implanted with data about the picture itself, for example, the camera producer and model, date and time the photograph was taken, the area, goals, and camera settings, among different subtleties. Utilizing this EXIF information, the programmers executed a bit of JavaScript that was covered in the "Copyright" field of the favicon picture. "Similarly as with different skimmers, this one likewise snatches the substance of the info fields where online customers are entering their name, charging address, and Visa subtleties," the scientists said. Beside encoding the caught data utilizing the Base64 position and turning around the yield string, the taken information is transmitted as a picture document to cover the exfiltration procedure. Expressing the activity may be the handicraft of Magecart Group 9, Malwarebytes included the JavaScript code for the skimmer is muddled utilizing the WiseLoop PHP JS Obfuscator library. This isn't the first run through Magecart bunches have utilized pictures as assault vectors to bargain web based business sites. Back in May, a few hacked sites were watched stacking a pernicious favicon on their checkout pages and in this manner supplanting the real online installment structures with a fake substitute that took client card subtleties. Mishandling DNS Protocol to Exfiltrate Data from the Browser :In any case, information taking assaults don't need to be essentially kept to malignant skimmer code.
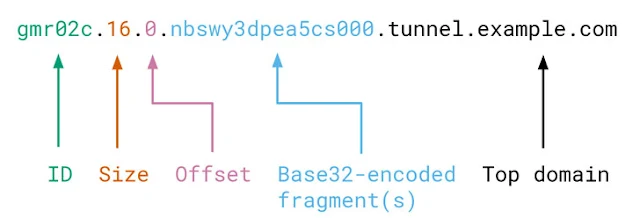
In a different procedure exhibited by Jessie Li, it's conceivable to appropriate information from the program by utilizing dns-prefetch, an inactivity decreasing strategy used to determine DNS queries on cross-starting point spaces before assets (e.g., documents, joins) are mentioned. Called "browsertunnel," the open-source programming comprises of a server that unravels messages sent by the instrument, and a customer side JavaScript library to encode and transmit the messages. The messages themselves are subjective strings encoded in a subdomain of the top area being settled by the program. The device at that point tunes in for DNS inquiries, gathering approaching messages, and interpreting them to extricate the important information. Put in an unexpected way, 'browsertunnel' can be utilized to hoard touchy data as clients do explicit activities on a site page and consequently exfiltrate them to a server by camouflaging it as DNS traffic. "DNS traffic doesn't show up in the program's investigating apparatuses, isn't obstructed by a page's Content Security Policy (CSP), and is regularly not reviewed by corporate firewalls or intermediaries, making it a perfect mode for carrying information in compelled situations," Li said.
Scott Morrison wouldn't state it, yet specialists are very glad to reprimand China for the "complex" digital assaults on Australian private and open associations. The PM affirmed Australia has been the objective of a digital assaults by a remote substance. "We realize it is a refined, state-based digital entertainer as a result of the scale and nature of the focusing on and the tradecraft utilized," Mr Morrison said on Friday. "Be that as it may, he declined to state which nation was behind the assaults. Inquired as to whether it was China, Mr Morrison stated: "The Australian government isn't making any open attribution about these issues. "We are extremely sure this is the activities of a state-based entertainer. "We have not gone any farther than that. I can't control what theory others may take part in."
Government sources had affirmed the aggressor was China, while Australian Strategic Policy Institute official executive Peter Jennings revealed to The Australian it was "clear" that the Asian mammoth was behind the digital assault. Assuming valid, it would include further grinding between the two nations, which have dropped out over the starting point of COVID-19, exchange and most as of late the condemning to death of an Australian medication dealer. Mr Morrison said these were not new digital dangers but rather were explicit, directed exercises and he needed to prompt Australians and associations so they can make a move to ensure themselves. He said the examinations led so far have not uncovered any enormous scope individual information breaks.
Australia's security organizations are working intimately with partners and accomplices to oversee it. "I addressed (British Prime Minister) Boris Johnson the previous evening about a scope of issues, including this one and there are various commitment with our partners for the time being," Mr Morrison said. The head administrator additionally addressed Opposition Leader Anthony Albanese on Thursday night on the issue, just as state and domain pioneers. "Digital assaults are a main problem," Mr Albanese told correspondents in the NSW town of Thredbo. "What the proof is, is that these assaults are relied upon to be all the more regularly." A month ago a joint articulation by the Department of Foreign Affairs and Trade and the Australian Cyber Security Center said there had been "inadmissible malevolent" digital action. "Of specific concern are reports that pernicious digital entertainers are trying to harm or hinder the activity of clinics, clinical administrations and offices, and emergency reaction associations outside of Australia," it said. Remark has been looked for from the Chinese international safe haven.