Is it accurate to say that you are an ordinary client of eBay, Amazon, and other online business sites? In the event that your answer is truly, perused along to know how programmers can take subtly redirect your card subtleties utilizing Google Analytics. What's happening? Programmers are utilizing Google's servers and Google Analytics stage to take charge card data. This is another strategy used to sidestep Content Security Policy (CSP) utilizing the Google Analytics API. There are Magecart assaults progressing that use this strategy to scratch Mastercard data from online business locales.
How accomplishes this work? Danger entertainers can utilize Google Analytics contents to take information. They utilize a web skimmer content that is intended to encode and scramble taken information and send it to the entertainer's Google Analytics dashboard. The assailants utilize their own Tag ID proprietor of the UA-#######-# structure since CSP doesn't segregate dependent on Tag ID. The base of the issue lies in the non-granular structure of the CSP rule framework. Significant details about Google Analytics Just 210,000 web spaces out of the best 3 million are utilizing CSP to ensure client information on their locales. Also, 17,000 locales reachable by means of these top spaces have whitelisted google-analytics.com. More than 29 million sites are allegedly utilizing Google Analytics administrations, while Yandex Metrika and Baidu Analytics are utilized on 2 million and 7 million locales, separately. What are the specialists saying?
Willem de Groot expressed, "CSP was created to restrain the execution of untrusted code. In any case, since essentially everyone confides in Google, the model is defective." Specialists recommend that an expected answer for this would originate from versatile URLs that would include ID as a piece of the URL. Basically CSP can't guarantee site security if programmers find shrewd approaches to sidestep it. Since areas like Google Analytics are trusted of course, it makes a helpless circumstance for most well known sites utilizing it.
The administration has gotten a report into Huawei that is probably going to change its approach over the Chinese association's job in the UK's telecoms systems. Advanced Secretary Oliver Dowden said GCHQ's National Cyber Security Center had conveyed its discoveries. NCSC is accepted to have said it can no longer guarantee the security of Huawei's items on account of new US sanctions. The Department for Digital, Culture, Media and Sport presently can't seem to convey its decisions to the head administrator, however Boris Johnson said on Monday evening that he didn't need the nation to be "powerless against a high-chance state merchant". Huawei has said it stays "open to conversations". Be that as it may, one of the organization's representatives took a harder line throughout the end of the week, following paper reports that the administration may boycott the acquisition of new Huawei 5G hardware before the year's over. "UK strategy is being directed by [the] Trump organization... shouldn't the US regard a United Kingdom in the post-Brexit time being in a situation to picked its own media transmission technique?" tweeted Paul Harrison, Huawei's head of worldwide media, UK. China's envoy to the UK has cautioned that if the nation disposed of Huawei, it would convey a more extensive message about its receptiveness to remote speculation. High-hazard seller Huawei's job in the UK appeared to have been settled in January, when the legislature put a top on its piece of the pie in versatile and full-fiber fixed-line broadband systems, and avoided its contribution in the most delicate pieces of 5G known as the "center"'. Be that as it may, the US therefore declared new authorizes that prohibit the Chinese firm and the outsiders that make its chips from utilizing "US innovation and programming to structure and assembling" its items. Washington claims Huawei is upheld by the Chinese military and represents a national security hazard, guarantees the organization denies. NCSC has analyzed the effect of the approvals, including the way that they adequately keep the organization from having the option to utilize basic programming to plan and reproduce chips before their creation, just as preventing outsider makers from having the option to utilize hardware expected to deliver a portion of Huawei's most exceptional processors. The hazard is that as an outcome Huawei would need to begin sourcing chips from somewhere else, which UK security authorities probably won't have the option to appropriately vet. He said an official choice presently couldn't seem to be taken, yet included: "We need to differentiate away from these alleged high-chance merchants, of which Huawei is the foremost one... we need to be in a position where we don't have high-hazard sellers in our systems by any stretch of the imagination." Mr Dowden said he intended to tell Parliament of any arrangement change before MPs rose for the late spring break on 22 July. 'Bear the results' It stays indistinct how far the legislature will go. The Sunday Times announced that BT and Vodafone had requested to be given until 2030 to expel Huawei's gear from their current 5G foundation. What's more, one of his partners, Bob Seely MP, told the Telegraph: "2029 will be excessively long for certain associates, who need to see Huawei out of the framework before the finish of this parliament." In principle, the Prime Minister could choose to go further, requesting Huawei's unit to be expelled from 3G and 4G arranges, and even the a huge number of side of the road cupboards it is as of now sits in giving broadband network. Yet, specialists have cautioned that the expense of this would run into "billions of pounds" and would make significant postponements the rollout of full-fiber web. At the point when gotten some information about this, Mr Johnson stated: "We need to concoct the privilege mechanical arrangements, yet additionally we should ensure that we can keep on conveying the broadband that the UK needs." A representative for the head administrator included that there was "no change to [the] broadband 2025 objective". China's presentation of a dubious security law giving it new controls over Hong Kong, and the ensuing capture of some genius popular government dissenters may put the leader constrained to take an intense position. Previous Labor business serve Peter Mandelson said the inevitable US sanctions - which are because of become effective in September - gave "a spread" for the UK to change its position. "President Trump has without a doubt prevailing with regards to toppling the administration's unique choice about Huawei gear in Britain's 5G arrange," he included. "This is generally not an issue of security. It's a business war between the US and China. "President Trump said he needed to crush Huawei, and he's doing as such through draconian approvals." "It will be significant for the UK to move skillfully to guarantee that we don't get constrained into settling on a parallel decision around there, in manners that could be negative to our drawn out intrigue," he said. When examined regarding the issue, China's diplomat to the UK said the more extensive Chinese business network was watching to perceive how the UK dealt with the case. "We need to be your companion. We need to be your accomplice," included Liu Xiaoming.
"In any case, on the off chance that you need to make China an antagonistic nation, you should bear the results." On Thursday, MPs will talk about the issue further at the House of Commons science and innovation board when it questions Huawei, Vodafone and BT about the ramifications of an expected boycott.
In what's one of the most inventive hacking efforts, cybercrime groups are presently concealing vindictive code inserts in the metadata of picture records to clandestinely take installment card data entered by guests on the hacked sites. "We discovered skimming code covered up inside the metadata of a picture record (a type of steganography) and secretly stacked by undermined online stores," Malwarebytes analysts said a week ago. "This plan would not be finished without one more fascinating variety to exfiltrate taken Visa information. Indeed, lawbreakers utilized the camouflage of a picture document to gather their plunder." The developing strategy of the activity, generally known as web skimming or a Magecart assault, comes as terrible on-screen characters are finding various approaches to infuse JavaScript contents, including misconfigured AWS S3 information stockpiling containers and abusing content security strategy to transmit information to a Google Analytics account under their influence. Utilizing Steganography to Hide Skimmer Code in EXIF: Relying upon the developing pattern of web based shopping, these assaults ordinarily work by embeddings noxious code into an undermined website, which clandestinely collects and sends client entered information to a cybercriminal's server, hence giving them access to customers' installment data.
In this week-old crusade, the cybersecurity firm found that the skimmer was not just found on an online store running the WooCommerce WordPress module yet was contained in the EXIF (short for Exchangeable Image File Format) metadata for a dubious area's (cddn.site) favicon picture. Each picture comes implanted with data about the picture itself, for example, the camera producer and model, date and time the photograph was taken, the area, goals, and camera settings, among different subtleties. Utilizing this EXIF information, the programmers executed a bit of JavaScript that was covered in the "Copyright" field of the favicon picture. "Similarly as with different skimmers, this one likewise snatches the substance of the info fields where online customers are entering their name, charging address, and Visa subtleties," the scientists said. Beside encoding the caught data utilizing the Base64 position and turning around the yield string, the taken information is transmitted as a picture document to cover the exfiltration procedure. Expressing the activity may be the handicraft of Magecart Group 9, Malwarebytes included the JavaScript code for the skimmer is muddled utilizing the WiseLoop PHP JS Obfuscator library. This isn't the first run through Magecart bunches have utilized pictures as assault vectors to bargain web based business sites. Back in May, a few hacked sites were watched stacking a pernicious favicon on their checkout pages and in this manner supplanting the real online installment structures with a fake substitute that took client card subtleties. Mishandling DNS Protocol to Exfiltrate Data from the Browser :In any case, information taking assaults don't need to be essentially kept to malignant skimmer code.
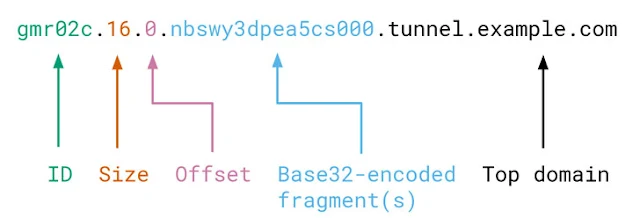
In a different procedure exhibited by Jessie Li, it's conceivable to appropriate information from the program by utilizing dns-prefetch, an inactivity decreasing strategy used to determine DNS queries on cross-starting point spaces before assets (e.g., documents, joins) are mentioned. Called "browsertunnel," the open-source programming comprises of a server that unravels messages sent by the instrument, and a customer side JavaScript library to encode and transmit the messages. The messages themselves are subjective strings encoded in a subdomain of the top area being settled by the program. The device at that point tunes in for DNS inquiries, gathering approaching messages, and interpreting them to extricate the important information. Put in an unexpected way, 'browsertunnel' can be utilized to hoard touchy data as clients do explicit activities on a site page and consequently exfiltrate them to a server by camouflaging it as DNS traffic. "DNS traffic doesn't show up in the program's investigating apparatuses, isn't obstructed by a page's Content Security Policy (CSP), and is regularly not reviewed by corporate firewalls or intermediaries, making it a perfect mode for carrying information in compelled situations," Li said.
Singapore's TraceTogether Tokens are the most recent exertion to handle Covid-19 with tech. Be that as it may, they have likewise reignited a security banter. The wearable gadgets supplement the island's current contact-following application, to recognize individuals who may have been contaminated by the individuals who have tried positive for the infection. All clients need to do is convey one, and the battery endures as long as nine months without requiring a revive - something one master said had "dazed" him. The administration office which built up the gadgets recognizes that the Tokens - and innovation all in all - aren't "a silver shot", yet should enlarge human contact-tracers' endeavors. The first to get the gadgets are a huge number of helpless old individuals who don't possess cell phones. To do as such, they needed to give their national ID and telephone numbers - TraceTogether application clients as of late needed to begin doing similarly. On the off chance that dongle clients test positive for the infection, they need to hand their gadget to the Ministry of Health in light of the fact that - not at all like the application - they can't transmit information over the web.
Human contact-tracers will at that point utilize the logs to recognize and prompt other people who may have been contaminated. "It's exceptionally exhausting in what it does, which is the reason I believe it's a decent plan," says equipment engineer Sean Cross. He was one of four specialists welcomed to examine one of the gadgets before they propelled. The gathering was indicated every one of its segments yet were not permitted to turn it on. "It can relate who you'd been with, who you've tainted and, vitally, who may have contaminated you," Mr Cross includes. Application help Singapore was the primary nation to send a national coronavirus-following application.
The nearby specialists state 2.1 million individuals have downloaded the product, speaking to about 35% of the populace. It is willful for everybody aside from transient laborers living in dormitories, who represent most of Singapore's 44,000 or more contaminations. The administration says the application helped it isolate a few people more rapidly than would have in any case been conceivable. In any case, by its own confirmation, the tech doesn't fill in just as had been trusted. On iPhones, the application must be running in the frontal area for Bluetooth "handshakes" to happen, which implies clients can't utilize their handsets for whatever else. It's likewise an enormous channel on the battery. Android gadgets don't confront a similar issue. Computerized contact-following can in principle be enormously compelling, however just if a huge level of a populace is included. Along these lines, proprietors of Apple's gadgets are probably going to be among others requested to utilize the dongles soon. Security concerns :At the point when the Token was first declared toward the beginning of June, there was an open reaction against the legislature - something that is a moderately uncommon event in Singapore. Wilson Low began an online appeal calling for it to be jettisoned. Just about 54,000 individuals have marked. "All that is preventing the Singapore government from turning into an observation state is the approach and ordering the necessary utilization of such a wearable gadget," the appeal expressed. "What comes next would be laws that express these gadgets must not be killed [and must] stay on an individual consistently - in this way fixing our destiny as a police state." Clergymen call attention to the gadgets don't log GPS area information or interface with portable systems, so can't be utilized for reconnaissance of an individual's developments. Mr Cross concurs that from what he was appeared, the dongles can't be utilized as area trackers. Be that as it may, he includes that the plan is still less security driven than a model advanced by Apple and Google, which is as a rule generally embraced somewhere else. "Toward the day's end, the Ministry of Health can go from this mysterious, mystery number that solitary they know, to a telephone number - to an individual," he clarifies. On the other hand, applications dependent on Apple and Google's model ready clients in the event that they are in danger, yet don't uncover their characters to the specialists. It is dependent upon the people to do so when, for instance, they register for a test.
Dr Michael Veale, an advanced rights master at University College London, cautions of the potential for mission creep. He gives a model where a legislature battling against Covid-19 should uphold isolate control. It could do as such, he says, by fitting Bluetooth sensors to open spaces to recognize dongle clients who are making the rounds when they ought to act naturally disconnecting at home. "You should simply introduce material science framework on the planet and the information that is gathering can be planned back to Singapore ID numbers," he clarifies. "The buildability is the stressing part." Be that as it may, the authority accountable for the organization liable for TraceTogether makes light of such concerns. "There is a high trust connection between the legislature and individuals, and there is information security," says Kok Ping Soon, CEO of GovTech. He includes that he trusts general society perceives that the wellbeing specialists need this information to secure them and their friends and family. Another explanation Singapore lean towards its own plan over Apple and Google's is that it can furnish disease transmission experts with more prominent understanding into a flare-up's spread. This was to a limited extent why the UK government at first opposed embracing the tech monsters' drive until its own push to work around Apple's Bluetooth limitations neglected to get by. In the event that Singapore's wearables fill in as trusted, different countries might be enticed to follow. you can settle on strategy choices which cautiously tie limitations or commitments just to high-hazard exercises. Else you're left with much blunter devices," remarks security master Roland Turner, another individual from the gathering welcomed by Singapore to examine its equipment. "There is maybe a confusing result that more noteworthy opportunities are conceivable."
Cybersecurity scientists today revealed new subtleties of watering gap assaults against the Kurdish people group in Syria and Turkey for observation and insight exfiltration purposes. The progressed steady danger behind the activity, called StrongPity, has retooled with new strategies to control traded off machines, cybersecurity firm Bitdefender. "Utilizing watering gap strategies to specifically taint casualties and sending a three-level C&C foundation to frustrate scientific examinations, the APT gathering utilized Trojanized famous devices, for example, archivers, document recuperation applications, remote associations applications, utilities, and even security programming, to cover a wide scope of alternatives that focused casualties may be looking for," the specialists said. With the timestamps of the dissected malware tests utilized in the crusade harmonizing with the Turkish hostile into north-eastern Syria (codenamed Operation Peace Spring) last October, Bitdefender said the assaults could have been politically propelled. Utilizing Tainted Installers to Drop Malware. StrongPity (or Promethium) was first freely investigated in October 2016 after assaults against clients in Belgium and Italy that pre-owned watering openings to convey malignant variants of WinRAR and True Crypt record encryption programming. From that point forward, the APT has been connected to a 2018 activity that manhandled Türk Telekom's system to divert several clients in Turkey and Syria to pernicious Strong Pity variants of legitimate programming.
Therefore when the focused on clients endeavor to download an authentic application on the official site, a watering opening assault or a HTTP divert is completed to bargain the frameworks. Last July, AT&T Alien Labs discovered proof of a new spyware crusade that abused trojanized renditions of WinBox switch the board programming and WinRAR record archives to introduce Strong Pity and speak with the enemy framework. The new assault technique recognized by Bitdefender continues as before: target casualties in Turkey and Syria utilizing predefined IP list by utilizing altered installers — including McAfee Security Scan Plus, Recuva, TeamViewer, WhatsApp, and Piriform's CCleaner — facilitated on limited programming totals and sharers. "Strikingly, all records explored relating to the spoiled applications seem to have been aggregated from Monday to Friday, during ordinary 9 to 6 UTC+2 working hours," the scientists said. "This fortifies Strong Pity could be a supported and sorted out engineer group paid to convey certain 'ventures.'" Once the malware dropper is downloaded and executed, the indirect access is introduced, which sets up correspondence with an order and control server for archive exfiltration and for recovering orders to be executed.
It additionally sends a "Record Searcher" part on the casualty's machine that circles through each drive and searches for records with explicit expansions (e.g., Microsoft Office reports) to be exfiltrated as a ZIP document. This ZIP record is then part into various covered up ".sft" scrambled documents, sent to the C&C server, and at last erased from the plate to cover any tracks of the exfiltration. Extending Beyond Syria and Turkey In spite of the fact that Syria and Turkey might be their common focuses on, the danger entertainer behind Strong Pity has all the earmarks of being extending their victimology to contaminate clients in Colombia, India, Canada, and Vietnam utilizing corrupted renditions of Firefox, VPNpro, Driver Pack, and 5kPlayer.
Calling it StrongPity3, Cisco Talos analysts yesterday depicted a developing malware toolbox that utilizes a module called "winprint32.exe" to dispatch the report look and transmit the gathered records. In addition, the phony Firefox installer likewise checks if either ESET or Bit Defender antivirus programming is introduced before dropping the malware. "These qualities can be deciphered as signs that this danger on-screen character could in truth be a piece of a venture administration for enlist activity," the specialists said. "We accept this has trademarks an expertly bundled arrangement because of the comparability of each bit of malware being amazingly comparable yet utilized across various focuses with minor changes."
Trump's xenophobic fantasy about structure a "major, lovely divider" along the Mexico–US fringe has drawn a stage nearer to (computer generated) reality. The White House simply hit an arrangement with Palmer Luckey's Anduril Industrial to raise an AI-fueled segment along the boondocks. Anduril will introduce many reconnaissance towers over the rough landscape. The columns will utilize cameras and warm imaging to recognize anybody attempting to enter "the place that is known for the free" and send their area to the cellphones of US Border Patrol specialists. US Customers and Border Protection affirmed that 200 of the towers would be introduced by 2022, despite the fact that it didn't make reference to Anduril by name, nor the expense of the agreement. Anduril officials disclosed to The Post that the arrangement merits a few hundred million dollars. "These towers give specialists in the field a critical advantage against the criminal systems that encourage illicit cross-fringe movement," said Border Patrol Chief Rodney Scott in an announcement. "The more our specialists think about what they experience in the field, the more securely and adequately they can react." In a portrayal of the framework that peruses like an excursions leaflet, the office said the towers were "completely appropriate for remote and provincial areas" work with "100 percent sustainable power source" and "give self-sufficient observation activities 24 hours out of each day, 365 days out of every year." Luckey, Thiel, and Trump Eminently, the towers don't utilize facial acknowledgment. Rather, they recognize development by means of radar, and afterward filter the picture with AI to watch that it's a human. Anduril claims it can recognize creatures and individuals with 97% precision. The organization is likewise sure that its framework has a drawn out future on the fringe — paying little mind to who wins November's presidential political race. Up-and-comer Joe Biden as of late called Trump's divider dream "costly, ineffectual, and inefficient," however Democrats have likewise communicated help for a less expensive, virtual obstruction. "Regardless of where we go as a nation, we're going to need to have situational mindfulness on the outskirt," Matthew Steckman, Anduril's main income official, revealed to The Post. "Regardless of if conversing with a Democrat or a Republican, they concur that this sort of framework is required." That is all the more uplifting news for Anduril, which this week saw its valuation jump to $1.9 billion in the wake of raising a $200 million subsidizing round. The organization was established in 2017 by Oculus designer Palmer Luckey. After he sold the VR firm to Facebook for $3 billion, Luckey was allegedly removed from the informal organization for giving $10,000 to a master Trump gathering so it could spread images about Hillary Clinton. Anduril is additionally upheld by another of Trump's huge amigos in huge tech: very rich person speculator and previous PayPal author Peter Thiel — who guarantees he's not a vampire. Be that as it may, even Thiel is thinking about dumping his inexorably unhinged and supremacist President. Maybe the huge check for Anduril will get him back installed the Trump Train.
It has been proposed that taking nutrient D may shield individuals from getting COVID-19. However, would it be a good idea for us to utilize enhancements to avert the infection? We have to isolate truth from fiction. Nutrient D is basic for keeping up by and large wellbeing, particularly for bones, teeth, and muscles. It directs the body's stores of calcium and phosphate and causes us keep up a solid resistant framework. While we can get nutrient D from sleek fish, egg yolks, red meat, and enhanced nourishments in our eating regimen, by far most of nutrient D in the body is delivered in the skin because of daylight introduction. Nutrient D focuses are lower in individuals with stoutness, those with hypertension or diabetes, and the individuals who smoke. It very well may be put away in fat cells, along these lines decreasing the circling fixation in the blood. Horrible eating routine in those with coronary illness and an inactive way of life away from daylight add to bring down blood convergences of the nutrient, while smoking influences nutrient D and calcium guideline. These conditions are related with expanded danger of COVID-19 and the more extreme types of the malady. It has hence been recommended that individuals with low nutrient D are at higher danger of disease or have more regrettable results with COVID-19. Northern half of the globe Among October and April, the greater part of Western Europe and the northern conditions of North America lie excessively far north to have enough daylight to give sufficient creation of nutrient D in the skin. Numerous individuals in these spots are in danger of getting inadequate during these a half year except if they get expanded degrees of the nutrient from their eating routine or enhancements. Toward the beginning of the pandemic, the northern side of the equator was rising up out of the winter a very long time of 2019-20. Additionally, with the lockdown, numerous individuals were disconnecting or protecting inside with almost no presentation to characteristic daylight. This will have negatively affected nutrient D focus, making a few people inadequate and therefore trading off resistant framework work. Italy, Spain, the UK, China, and a few pieces of North America all have a high extent of the populace with nutrient D inadequacy. These nations additionally have essentially higher quantities of COVID-19 passings. Different nations in a similar locale, for example, Norway, Denmark, and Finland have lower COVID-19 death rates, however more elevated levels of nutrient D in the populace as supplementation and stronghold of food in these nations are normal.
It has likewise been featured that individuals from Black, Asian, and minority ethnic (BAME) foundations make up an enormous extent of patients with extreme COVID-19 requiring escalated care in the UK. Low convergence of nutrient D in BAME individuals in the northern side of the equator may add to more serious hazard, nonetheless, babies and offspring of every single ethnic foundation who are frequently nutrient D insufficient don't have a more serious danger of COVID-19. Further information examination, explicitly taking a gander at ethnicity and nutrient D in COVID-19, would be expected to make firm inferences, and the segregation looked by these populaces can't be ignored. Rewarding COVID-19? Scientists have joined writing look with factual cross-sectional investigations to evaluate the impact of nutrient D level on COVID-19. Some recommend there is no proof to help nutrient D dosing in forestalling COVID-19 while others have delivered proof for supporting the utilization of enhancements. What is evident is that we need progressively devoted investigations to evaluate any connection between nutrient D and COVID-19. At present, 28 preliminaries have been enlisted identifying with nutrient D and COVID-19. The detailing of these discoveries will better guide the administration of patients giving low groupings of nutrient D. In spite of the fact that nutrient D is useful to wellbeing, it ought to be noticed that an excessive amount of can be harmful and can cause parchedness, expanded thirst, retching, stomach cramps, and mental disarray. There have been reports that taking exceptionally huge dosages (supposed "megadoses") of nutrient D enhancements will forestall COVID-19 contamination. This is essentially false. There is no logical proof to help huge portions of nutrient D being defensive enough to exceed the harmful impacts. We don't yet have a full away from of the connection between nutrient D and COVID-19, however in the event that your blood focuses are low, or you are protecting out of direct daylight, it's never a poorly conceived notion to see your primary care physician about taking enhancements – simply don't take too much.
Early a week ago, bits of gossip that internet business goliath Amazon would purchase a self-sufficient vehicle startup began to surface. Before the week's over, it was a done arrangement. Be that as it may, what is Amazon doing purchasing an independent vehicle startup? As indicated by a Financial Times report, Amazon as of late paid $1.2 billion to get self-driving tech up-and-comer, Zoox. This makes it Amazon's greatest attack into self-driving tech, and one of the organization's greatest acquisitions ever. I should be straightforward here, Zoox isn't one of the new businesses in this field positions high on my radar, so how about we investigate the organization before attempting to make sense of what Amazon is doing. Zoox was shaped in 2014 and is situated in California. The organization was begun with the objective of making a self-sufficient vehicle explicitly for the "robotaxi" showcase. Consider them expected contenders to any semblance of Alphabet's (previously Google's) Waymo, Yandex, and Uber's self-driving division. What makes Zoox one of a kind however, is that the organization is building up its own vehicle as well. Most self-driving organizations center around creating programming and sensors to retrofit to existing vehicles. Right now the organization has been retrofitting Toyotas, however with plans to uncover its introduction vehicle in the not so distant future. After some grievous cutbacks due to coronavirus, Zoox now has around 900 staff taking a shot at its self-driving tech. Until now, the organization has apparently brought around $1 billion up in startup capital, and two or three years prior was esteemed at over $3 billion. It would seem that Amazon may have somewhat of a decent arrangement here, or constantly underestimated Zoox, yet how can it hope to get its cash back? In its official declaration of the securing, Amazon said that it's purchased the startup to help Zoox understand its fantasy. I question that is the genuine explanation, organizations don't accepting different organizations just to get them out. Amazon could have contributed, however no, it purchased the organization. In addition, Zoox, an organization that is had a past valuation of multiple times what Amazon paid, acknowledged the arrangement. Something lets me know there's more going on here than we've been told. What precisely however, stays muddled. The web based business goliath has just dunked its toe in the apply autonomy and electric vehicle world, however not both simultaneously. In 2012, Amazon purchased Kiva Systems, an organization that made stockroom robots for moving merchandise around business structures. In February a year ago, Amazon put around $440 million into EV startup Rivian to fabricate an armada of practical electric conveyance vans.
Amazon doesn't generally have a lot to pick up on its current plan of action by building a robot taxi division. Many have really scrutinized the plan of action of robotaxis, asserting that they're not really going to be that gainful contrasted with normal human-driven taxicabs. In the last quarter of 2019, Amazon spent almost multiple times ($9.6 billion) what it spent on Zoox just on conveying merchandise to clients. That makes its obtaining of Zoox appear as though pocket change in examination. For Amazon, an online business organization, the genuine cash to be made is in conveyance frameworks. Or then again rather having the option to convey more, with less human inclusion, since people need rest, robots don't. Rather, the organization could and ought to investigate self-sufficient tech for conveyances. Envision the potential if Amazon could get Rivian, Kiva (presently Amazon Robotics), and Zoox in a room together. Rivian is creating one of the most long awaited electric trucks, the R1T. Be that as it may, as per various reports, Zoox's invasion into vehicle improvement has left a great deal to be wanted. Maybe the more drawn out term desire is that Amazon can tie all these specialty units together, to make one sound supportable and self-governing conveyance division.
Think more along the lines of Nuro's agonizingly charming driverless conveyance robot, and I believe we're getting some place. In any case, Amazon said that it will leave Zoox to its own gadgets to keep on building its own vehicle and self-driving tech. In any case, if Amazon needs to bring in its cash back, it ought to get Zoox dealing with creating conveyance robots to cut that huge transportation bill. Amazon has all the bits of the riddle, it simply needs to assemble them.